- Prerequisites
- Step 1. Create new gateway device on ThingsBoard
- Step 2. Enable remote logging
- Step 3. Add new connector
- Step 4. Check device data
- Configure other connectors
- (Optional) Import gateway widgets bundle and dashboard
- Next steps
The ThingsBoard IoT Gateway is an open-source solution, designed to serve as a bridge between IoT devices connected to legacy and third-party systems with ThingsBoard.
This guide covers initial IoT Gateway installation and configuration, we will do the following things:
- Create a new gateway device using ThingsBoard IoT Gateways dashboard;
- Launch the gateway using Docker command;
- Configure different connector types (MQTT, OPC-UA, Modbus) in order to connect to a local demo servers and read data from them;
- Check received device data on ThingsBoard.
Prerequisites
- Before initiating the Gateway setup, ensure that the ThingsBoard server is up and running. The simplest approach is to utilize the Live Demo or ThingsBoard Cloud. Alternatively, you can install ThingsBoard manually by following the steps outlined in the Installation Guide.
- Before moving forward, ensure Docker is installed and properly configured on your machine. If you haven’t installed Docker yet, you can download it from the official Docker website and follow their installation guide for your specific operating system.
- If you don’t have a dashboard installed, you can download Gateway widget bundle JSON file here and ThingsBoard IoT Gateways dashboard JSON file here. Use this guide to import gateway widgets bundle and dashboard.
Step 1. Create new gateway device on ThingsBoard
First, add a gateway device to your ThingsBoard instance by following these steps:
-
Go to “Dashboards” tab and open “ThingsBoard IoT Gateways” dashboard.
-
Click the “+” button, enter the gateway device name (e.g., “My Gateway”), and select the device profile.
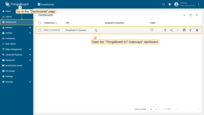
Go to “Dashboards” tab and open “ThingsBoard IoT Gateways” dashboard.
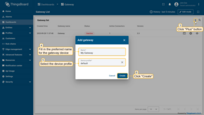
Click the “+” button, enter the gateway device name (e.g., “My Gateway”), and select the device profile.
To launch the gateway, use the following steps:
-
On the gateway dashboard, click on “Launch command” button in the top right corner.
-
Click to download docker-compose.yml file to your PC, copy command and execute it in your terminal.
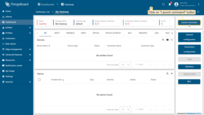
On the gateway dashboard, click on “Launch command” button in the top right corner.
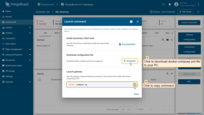
Click to download docker-compose.yml file to your PC, copy command and execute it in your terminal.
After running gateway docker image, you can see the following logs in your terminal:

Step 2. Enable remote logging
To view gateway and connector logs on the dashboard, you need to enable remote logging. For this purpose, use the following steps:
-
On the gateway dashboard, click on “General configuration” button on the right panel.
-
Navigate to the “Logs” tab. Enable the “Remote logs” toggle. Select “DEBUG” in the “Log level” drop-down menu.
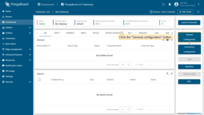
On the gateway dashboard, click on “General configuration” button on the right panel.
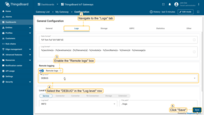
Navigate to the “Logs” tab. Enable the “Remote logs” toggle. Select “DEBUG” in the “Log level” drop-down menu.
Step 3. Add new connector
By choosing the type of connector, you determine the specific method of connection you will use to ensure the interaction of your gateway with other systems or devices.
To see how the connector works, you can choose one of the following connectors:
Let’s add an MQTT connector, which will subscribe to some data topics using the demo broker with a built-in data generator and send data to the gateway. Setup demo MQTT brokerAs a demo MQTT broker, we will use docker image, that can be installed and run using the following command: After running docker image, you can see the following logs in your terminal:
Setup connectorMQTT connector will establish a connection to a broker named “Demo Broker” at “host.docker.internal” on port 1884, using an anonymous security type. It will include a data mapping for the “data/” topic, specifying a JSON converter and defining attribute and time series mappings for device data. Additionally, it will handle connect and disconnect requests for sensors with expressions to extract device names from topic filters. To create a connector, follow these steps:
 Click on “Connectors configuration” button on the right panel;  Click the “+ Add connector” button;  Choose “MQTT” connector type from the dropdown, fill in “Name” field, choose “Logging level” to INFO, disable “Fill configuration with default values” field and click on “Add” button;  Connector created. First, we need to configure the connection to the demo broker. Let’s start from the “Connection to broker” section. This section offers detailed connection configuration options and contains several important fields, including host, port, MQTT version, client ID, and security settings. The host field specifies the address of the broker, while the port field indicates the communication port. The MQTT version field ensures compatibility with the protocol version being used. The client ID uniquely identifies the client, and the security settings provides configuration for client authorization at MQTT Broker. Fill in the following fields with values:
 First, we need to configure the connection to the demo broker. Let’s start from the “Connection to broker” section. This section offers detailed connection configuration options and contains several important fields, including host, port, MQTT version, client ID, and security settings. The host field specifies the address of the broker, while the port field indicates the communication port. The MQTT version field ensures compatibility with the protocol version being used. The client ID uniquely identifies the client, and the security settings provides configuration for client authorization at MQTT Broker. Then, click “Save”.
Let’s configure data map using the following steps:
 Click “Connectors configuration” button on the right panel.  In the opened window, fill in the “Topic filter” field with “data/”, select the “QoS” field to “0 - At most once”, and select the “Payload type” to JSON.
 Scroll down to “Data conversion” section. For “Device” subsection use the following options/values: In the Name row, select “Constant” in the “Source” dropdown field, fill in the “Value / Expression” field with the “Device Demo” value. In the “Profile name” row, select “Constant” in the “Source” dropdown field, fill in the “Value / Expression” field with the “default” value.
 Click on pencil icon opposite to “Attributes” subsection;  Click on “Add attribute” button;  Fill in “Key” field with “frequency” value, select “Integer” option in “Type” field and fill in “Value” field with “${frequency}” value. Click on “Add attribute” button again;  Fill in “Key” field with “power” value, select “Integer” option in “Type” field and fill in “Value” field with “${power}” value. Click on “Apply” button.
 Click on pencil icon opposite to “Time series” subsection;  Click on “Add time series” button;  Fill in “Key” field with “temperature” value, select “Integer” option in “Type” field and fill in “Value” field with “${temperature}” value. Click on “Add time series” button again;  Fill in “Key” field with “humidity” value, select “Integer” option in “Type” field and fill in “Value” field with “${humidity}” value. Click “Apply” button;  Click “Add” button;  Data mapping added.
But for now, we need only connect and disconnect requests. Let’s configure requests map using the following steps:
 Click on “Add mapping” button;  In the opened window, select “Connect request” in the “Request type” dropdown field, fill in “Topic filter” with “sensor/connect” value. For “Device” subsection use the following options/values: in the “Name” row, select “Extract from message” in the “Source” dropdown field, fill in the “Value / Expression” field with the “${SerialNumber}” value; in the “Profile name” row, select “Constant” in the “Source” dropdown field, fill in the “Value / Expression” field with the “default” value. Click on “Add” button;  Mapping added. Now, let’s add another connect request using the following steps:
 Click on “+” button;  select “Connect request” in the “Request type” dropdown field, fill in “Topic filter” with “sensor/+/connect” value. For “Device” subsection use the following options/values: in the “Name” row, select “Extract from topic” in the “Source” dropdown field, fill in the “Value / Expression” field with the “(?<=sensor\/)(.*?)(?=\/connect)” value; in the “Profile name” row, select “Constant” in the “Source” dropdown field, fill in the “Value / Expression” field with the “default” value. Click on “Add” button.;  Mapping added. And finally, let’s add disconnect requests. For this purpose, follow the steps below:
 Click on “+” button;  In the opened window, select “Disconnect request” in the “Request type” dropdown field, fill in “Topic filter” with “sensor/disconnect” value. For “Device” subsection use the following options/values: in the “Name” row, select “Extract from message” in the “Source” dropdown field, fill in the “Value / Expression” field with the “${SerialNumber}” value. Click on “Add” button;  Mapping added. Now, let’s add another disconnect request using the following steps:
 Click on “+” button;  In the opened window, select “Disconnect request” in the “Request type” dropdown field, fill in “Topic filter” with “sensor/+/disconnect” value. For “Device” subsection use the following options/values: in the “Name” row, select “Extract from topic” in the “Source” dropdown field, fill in the “Value / Expression” field with the “(?<=sensor\/)(.*?)(?=\/disconnect)” value. Click on “Add” button;  Mapping added. Click “Save” button.
Following the steps outlined, your gateway will receive and apply the new configuration. It will then synchronize its state with the remote server. You can view the synchronization status of the connector configuration in the “Configuration” column, which will indicate whether the gateway is successfully aligned with the remote settings. Also, you can see the connector logs to make sure that the connector works, for this purpose, follow these steps:
 Click on logs icon to open connector logs page;  You can see the “Logs” table that consists of “Created time”, “Status” and “Message” columns. For now, the gateway is ready to process data through the newly created and configured MQTT connector. Let’s publish data to the MQTT Broker defined in the configuration above, you can follow these steps using a tool like mosquitto_pub or an MQTT client library in your preferred programming language. In this example, we’ll use the mosquitto_pub command-line tool. 1.Ensure that the Mosquitto MQTT clients are installed on your system. Typically, you can install them using the package manager of your operating system:
2.Use the mosquitto_pub command to publish data to a specific MQTT topic. In this case, we’ll use the “data/” topic as defined in the configuration: Where:
Adjust the payload values as needed. |
Let’s add an OPC-UA connector, which will read some data from the demo server to the created gateway. Setup demo serverAs a demo simulation server, we will use docker image, that can be installed and run using the following command: After running docker image, you can see the following logs in your terminal:
Setup connectorThis OPC-UA connector configuration establishes a connection to a server named “OPC-UA Demo Server” at “opc.tcp://host.docker.internal:4840/freeopcua/server/”. The configuration specifies various settings, including timeouts, scan periods, and security mechanisms such as “Basic128Rsa15” with anonymous identity. The mapping section defines how OPC-UA nodes are mapped to devices and their attributes and time series. In this case, a device with the name “Demo Device” and type “default” is mapped to nodes under “Root.Objects.MyObject”. Attributes such as frequency and power, as well as time series like temperature and humidity, are mapped to specific paths in the OPC-UA server. Additionally, the configuration supports RPC methods and attribute updates. To create a connector, follow these steps:
 Click on “Connectors configuration” button on the right panel;  Click the “+ Add connector” button;  Choose “OPCUA” connector type from the dropdown, fill in “Name” field, choose “Logging level” to “INFO”, turn off the “Fill configuration with default values” option and click on “Add” button;  Connector created. First, we need to configure the connection to the demo OPC-UA server. Let’s start from the “Server” tab. This section offers detailed connection configuration options and contains several important fields, including server endpoint url, security settings, scan period, poll period, subscriptions settings and other.
Now, we are ready to move to the “Data mapping” section. This configuration section contains list of nodes that the gateway will subscribe to after connecting to the OPC-UA server, along with settings for processing data from these nodes. Let's add new node using the following steps:
 Go to the “Data mapping” tab, and click “Add mapping” button;  Fill in the fields with values taken from the documentation. Let's move to “Attributes” section to add “frequency” and “power” attributes. The configuration in this unit provides settings for processing data from OPC-UA server. These settings will be interpreted in ThingsBoard platform instance as attributes of the device. Also we will use path for finding corresponding node. Let's configure attribute section using the following steps:
 Click on the “pencil” icon in the “Attributes” section;  In the opened window, click on the “Add attribute” button;  Fill in the “Key” field with the “frequency”, select the “Type” field to the “Path”, and fill in the “Value” with the “${Frequency}”. Let's add another attribute. Collapse the recently added “frequency” attribute, click the “Add attribute” button, and fill in the fields with the following values, using the same process as before:
Click the “Apply” button after you've completed the configuration.  Collapse the recently added “frequency” attribute, and click “Add attribute” button to add another attribute;  Fill in the fields with values taken from the documentation. Then, click “Apply”. We finish with the “Attributes” section, so let's move to the “Time series” section. The configuration in this unit provides settings for processing data from the OPC-UA server. These settings will be interpreted in ThingsBoard platform instance as time series of the device. Let's configure time series section using the following steps:
 Click on the “pencil” icon in “Time series” section;  In the opened window, click on “Add time series” button;  Fill in the fields with values taken from the documentation. Let's add another attribute. Collapse the recently added “temperature” time series, click the “Add time series” button, and fill in the fields with the following values, using the same process as before:
 Collapse the recently added “temperature” time series, and click “Add time series” button to add another time series;  Fill in the fields with values taken from the documentation. Then, click “Apply”. The final view of your configured connector will look like on the following image. Click the “Add” button after you've completed the configuration.  The final view of your configured connector. Click the “Add” button after you've completed the configuration. Finally, save the OPC-UA configuration by clicking the “Save” button. Following the steps outlined, your gateway will receive and apply the new configuration. It will then synchronize its state with the remote server. You can view the synchronization status of the connector configuration in the “Configuration” column, which will indicate whether the gateway is successfully aligned with the remote settings.  You can view the synchronization status of the connector configuration in the “Configuration” column, which will indicate whether the gateway is successfully aligned with the remote settings. Also, you can see the connector logs to make sure that the connector works, for this purpose, follow these steps:
 Click on logs icon to open connector logs page;  You can see the “Logs” table that consists of “Created time”, “Status” and “Message” columns. For now, the gateway is ready to process data through the newly created and configured OPC-UA connector. |
Step 4. Check device data
To review the data uploaded from your gateway, use the following steps:
-
Navigate to the Devices page and click on the created device. This will open the device details page. From there, switch to the “Attributes” tab to view the attributes that were configured in the connector.
-
To view real-time telemetry data from the device, navigate to the “Latest Telemetry” tab. Here, you will find the telemetry data being sent by the device, including metrics like “humidity” and “temperature”. This tab provides real-time device telemetry updates.
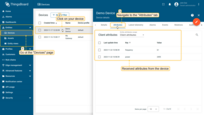
Navigate to the Devices page and click on the created device. This will open the device details page. From there, switch to the “Attributes” tab to view the attributes that were configured in the connector.
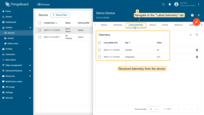
To view real-time telemetry data from the device, navigate to the “Latest Telemetry” tab. Here, you will find the telemetry data being sent by the device, including metrics like “humidity” and “temperature”. This tab provides real-time device telemetry updates.
Configure other connectors
After the successful installation and configuration of your first connector, you can configure other connectors to connect to different devices. You can find more information about connectors in the following articles:
- MQTT connector
- OPC-UA connector
- Modbus connector
- BLE connector
- Request connector
- REST connector
- CAN connector
- FTP connector
- Socket connector
- XMPP connector
- BACnet connector
- OCPP connector
- ODBC connector
- SNMP connector
- Custom connector
More about ThingsBoard IoT Gateways Dashboard, you can read here.
(Optional) Import gateway widgets bundle and dashboard
First, we have to import gateway widgets bundle, for this purpose, use the following steps:
-
Go to the “Widgets Library” page, and click the “+” button in the upper right corner of the “Widgets Bundles” page. Select “Import widgets bundle” from the drop-down menu.
-
You will be prompted to upload the downloaded gateway widgets bundle JSON file in the pop-up. Drag and drop a file from your computer, then click “Import” to add a widget bundle to the library.
-
The widgets bundle is imported.
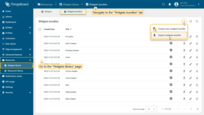
Go to the “Widgets Library” page, and click the “+” button in the upper right corner of the “Widgets Bundles” page. Select “Import widgets bundle” from the drop-down menu.
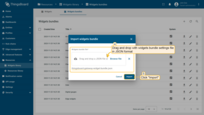
You will be prompted to upload the downloaded gateway widgets bundle JSON file in the pop-up. Drag and drop a file from your computer, then click “Import” to add a widget bundle to the library.
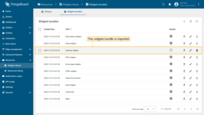
The widgets bundle is imported.
To import ThingsBoard IoT Gateways dashboard, follow these steps:
-
Go to the “Dashboards” page and click on the “+” button in the upper right corner of the page and select “Import dashboard” from the drop-down menu;
-
In the import dashboard window, upload the downloaded gateway dashboard JSON file and click “Import”.
-
Dashboard imported. Click on the row with the dashboard name to open it.
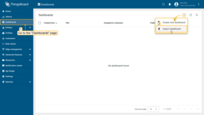
Go to the “Dashboards” page and click on the “+” button in the upper right corner of the page and select “Import dashboard” from the drop-down menu;
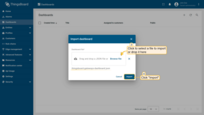
In the import dashboard window, upload the downloaded gateway dashboard JSON file and click “Import”.
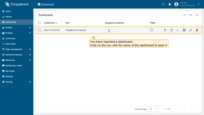
Dashboard imported. Click on the row with the dashboard name to open it.
Next steps
Explore guides related to main ThingsBoard features:
- Data Visualization - how to visualize collected data.
- Device attributes - how to use device attributes.
- Telemetry data collection - how to collect telemetry data.
- Using RPC capabilities - how to send commands to/from devices.
- Rule Engine - how to use rule engine to analyze data from devices.























